A new type of wireless transceiver is on its way to making data transmitted by brain-computer interfaces more secure.
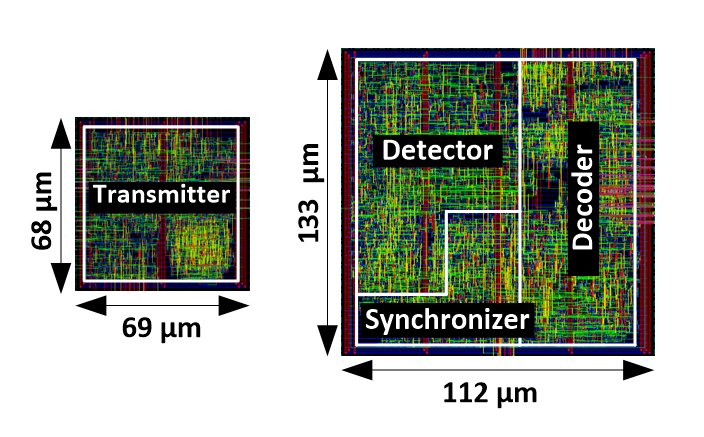 Photo: Chip layouts of the secure CSR-UWB transmitter and receiver in a 32nm CMOS (Complementary Metal Oxide Semiconductor) technology.
Photo: Chip layouts of the secure CSR-UWB transmitter and receiver in a 32nm CMOS (Complementary Metal Oxide Semiconductor) technology.
Online data security has been a public concern for some time now. Whether it’s hacking of business or government entities, concerns around social media data mining or even complex forms of malicious software, it’s become clear that personal information can be compromised through either a direct or indirect online attack. Hacking computer networks to obtain sensitive information is an all too frequent occurrence, and it can be damaging in many different ways.
Vulnerabilities can exist wherever there is a flow of sensitive information between computers, whether the data is transmitted via wires or wirelessly. Brain-computer interfaces (BCIs) are no exception to this rule and are therefore also exposed to the risk of being hacked, if adequate steps to ensure security are not taken. Center for Sensorimotor Neural Engineering (CSNE) members have been working on this issue by pioneering BCI security research in the VLSI Design and Test Laboratory at San Diego State University and the University of Washington’s UW BioRobotics Lab.
Recently, research by CSNE member, Amirhossein (Amir) Alimohammad, and his research assistant, Andrew Hennessy, at San Diego State University has taken things a step further in the effort to engineer low-power, compact and wireless BCIs that are also safe and secure from hackers. Alimohammad’s and Hennessy’s new paper in IEEE Transactions on Circuits and Systems presents an innovative transceiver design that offers more secure protection from hacking.
“We have been working on security of information,” Alimohammad said, “because when you are transmitting neural information wirelessly to an outside receiver, that information should be transmitted securely, so no one can actually pick up those neural signals and interpret it and understand what you are thinking, or what your purpose is.”
The transceiver Alimohammad and Hennessy are working on is part of a BCI chip designed to be implanted on the surface of the brain. The chip communicates neural information wirelessly to a receiver outside the body, such as a smartphone, for data processing. When this information is transmitted without security protections, data can be vulnerable to passive adversaries, digital eavesdroppers that would attempt to collect the transmitted information intended for the receiver, and active adversaries, hackers who would attempt to mimic the transceiver and send their own messages to the receiver while posing as the transmitter.
Conventional security practices typically use a security key to encrypt data before it is transmitted; however, the strict size and power requirements of brain-implantable transceivers prevents the use of conventional cryptography algorithms. Because conventional approaches are not a viable option, the security strategy of Alimohammad’s and Hennessy’s transceiver relies on changing the physical properties of the wireless transmission itself to mask the transmitted data.
This new transceiver uses a transmission scheme called digital code-shifted reference (CSR), which is a way of manipulating the properties of the transmitted wireless signal. The transceiver also takes advantage of a radio technology called ultra-wideband (UWB), which can use a very low energy level for short-range, high-bandwidth communications over a large portion of the radio spectrum. UWB is considered to provide some inherent advantages when it comes to the security of its transmissions. Pulses sent via UWB are incredibly narrow and reside at the noise level for other transmission methods, and this allows the pulses to have a naturally low probability of detection and interception; however, this inherent level of security is not an adequate substitution for cryptography and for potentially sensitive applications, such as bio-medical devices. This is where CSR comes in. CSR provides an added layer of security for the transceiver by randomizing the transmitted data pulses in ways only discernible to the intended receiver.
The security of the transceiver is based on separating a data and a reference pulse within transmitted information, so only a legitimate receiver would be able to discern the data pulse. To interpret the received data, the receiver must know what the separation is and use an exact timing delay to correlate the data with its reference.
“This movement in time serves as the basis for CSR, where we use orthogonal codes to separate a pulse randomly from a reference pulse in the code domain,” Alimohammad said. “So basically, we both [the transceiver and the receiver] are going to use the shared security key to define the separation in the code domain between a reference pulse and the data pulses, and only we [the transceiver and the receiver] know the correct orthogonal codes to apply to separate the pulses in time. No one else can figure it out, or it’s difficult…it’s extremely difficult to break.”
Alimohammad’s and Hennessy’s research has demonstrated that the CSR-UWB transceiver they engineered can successfully provide secure wireless transmissions in a compact, low-power format suitable for implantation in medical devices such as BCIs. Future research goals include even further reducing the size of the transceiver and finding ways to prevent hackers from using an active jammer to disable device transmissions.
“We want people to be able to implant these electronic transceivers safely,” Alimohammad said, “knowing that they are secure from hacking.”
For more information about the CSNE’s work in neural security and the CSR-UWB transceiver described in this article, contact Amir Alimohammad.
